A critical vulnerability nicknamed ?Heartbleed? was discovered in OpenSSL, the most popular SSL module used on Linux / cPanel servers. This exploit allows a third party to steal information that would otherwise be secured and encrypted with the SSL/TLS protocol, and to steal the private keys from the certificate pair itself.
Here’s a great site where you can learn more about the vulnerability: https://heartbleed.com/.
We’ve implemented updates in all areas where our systems were using affected versions of OpenSSL, and we are following best practices. We have also re-keyed all certificates on our web servers.
Important Facts
1. This is not a vulnerability with SSL/TLS or Namecheap.
2. SSL/TLS is not broken, nor are the digital certificates issued by Comodo and Symantec and their brands through Namecheap.
3. Users of OpenSSL versions 1.0.1 through 1.0.1f with the heartbeat extension enabled are affected.
4. OpenSSL version 1.0.1g addresses the vulnerability, as well as OpenSSL instances compiled without the heartbeat extension.
How does this impact Namecheap customers?
As a precaution to protect your data, we highly recommend that all Namecheap users change their account passwords. The rest depends on the type of services you have with Namecheap:
Hosting-only customers
We have already taken care of the OpenSSL update on all of our managed servers. If you are using an unmanaged hosting type, you can learn more here:
https://secure.pamirwebhost.com/serverstatus.php
SSL Certificate customers
First of all, if you are not using OpenSSL on your servers (or are not hosted on one of our Shared hosting plans), you are not affected.
If you do use OpenSSL, we strongly advise the following:
1. Identify which servers are running OpenSSL (versions 1.0.1 through 1.0.1f are affected).
2. Update to the latest patched version of the software (1.0.1g), or recompile OpenSSL without the heartbeat extension, if applicable.
3. Reissue any SSL certificates on affected web servers after moving to a patched version of OpenSSL.
4. Test your SSL installations.
5. Revoke any certificates that were replaced. Please revoke AFTER the reissue has been completed and you have successfully installed it on your web server.
6. Consider resetting end-user passwords that may have been visible in a compromised server memory.
7. Always refer back to this KB Article for more information.
How to Reissue and Revoke Certificates with Namecheap
Reissue Procedure
Reissuance is done from within your SSL Provider account and is free of charge.
Revocation Procedure
Once the certificate is reissued and successfully installed, the original certificate (the one that could be stolen) must be revoked, so that attackers can’t use it to impersonate you.
Certificates are revoked in several different ways, based on certificate brand:
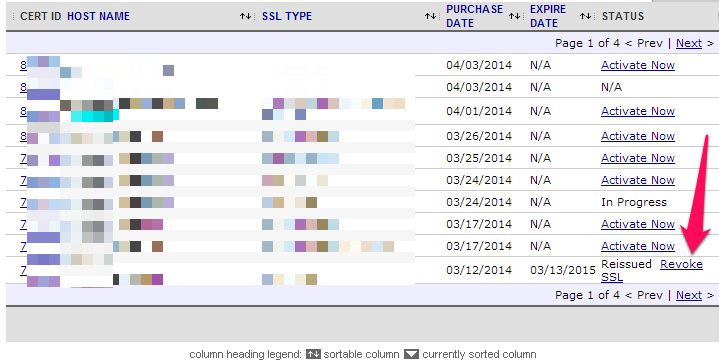
Comodo Certificates
In order to revoke Comodo certificates use ‘Revoke SSL’ button next to a reissued certificate in the list of your SSL certificates:
GeoTrust and RapidSSL Certificates
In order to have any GeoTrust (QuickSSL Premium, True BusinessID, TrueBusinessID EV, TrueBusinessID Multi Domain, True BusinessID EV Multi Domain, True BusinessID WildCard) or RapidSSL certificate reissued, please submit a ticket with revocation request to our ?SSL Certificates — Technical Support? team, here: https://secure.pamirwebhost.com/submitticket.php.
(Note: We will perform manual revocation of all certificates reissued between April 7 and April 10. After April 10, we will perform revocations based on ticket support requests only.)
Symantec and Thawte certificates
For Symantec and Thawte certificates, you can use the self-service revocation process.
(Note: We will perform manual revocation of all certificates reissued between April 7 and April 10. After April 10, all certificates must be revoked via the self-service process.)
1. To have Symantec and Thawte certificates revoked, please go to End User Home Portal. Links to End User Home Portal for each certificate brand:
Thawte – https://products.thawte.com/orders/orderinformation/authentication.do?
Symantec – https://products.verisign.com/orders/orderinformation/authentication.do?
2. You will be asked to enter the following information:
– Fully qualified domain name (Common Name) of the certificate or the Order ID. This refers to the Certificate Authority’s ID; Namecheap Order IDs will not work here. Please use common name field.
– Email address. This refers to admin contact email, as specified during the last activation step. It’s the address where you received your certificate.
– The 5-digit number displayed in the image
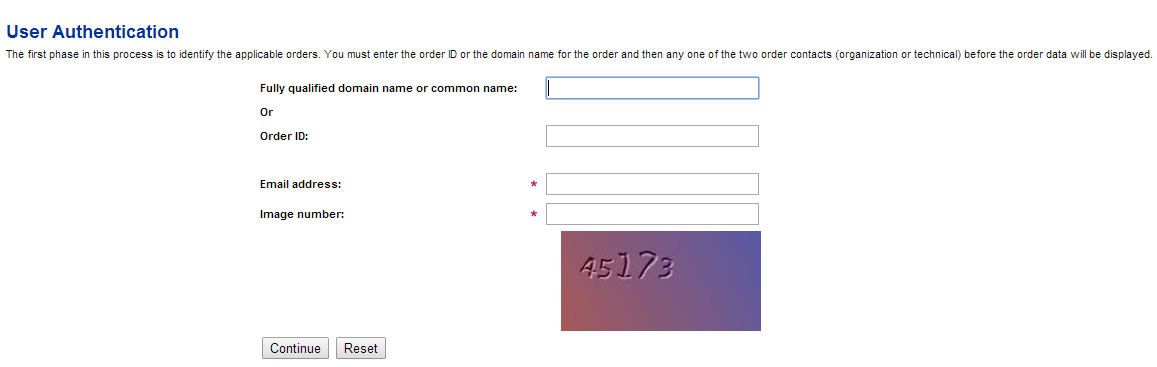
3. Click Continue. A list of all certificates that meet the Common Name and contact email criteria will appear.
4. Under the View Order Information column, click the Request Access button next to the order being reissued.
5. An email will be sent to the contact email address provided, with a link to the Order Access page.
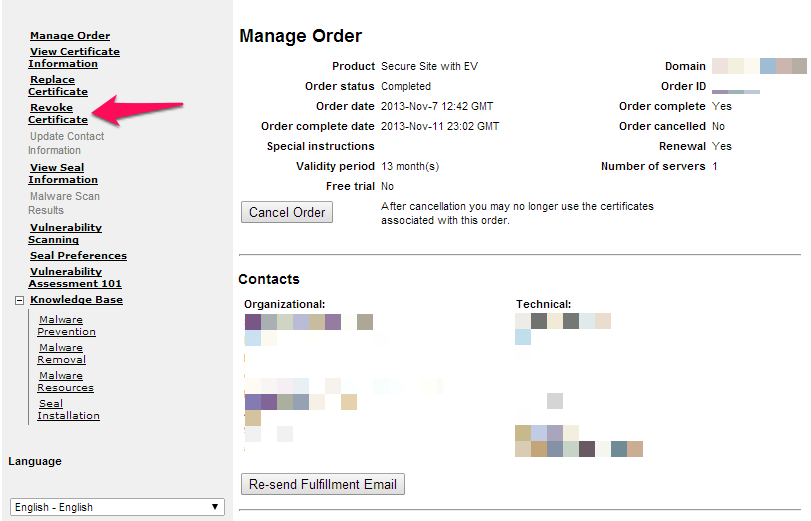
6. Click the link to access the page. The details of the certificate order will appear.
7. To revoke a certificate: On the left-hand side of the page, click Revoke Certificate.
9. On the next page, check the box next to the certificate you want to revoke. Make sure you are revoking the older, reissued certificate. The newest certificate will be at the top of the list. Please check the lower one(s), as shown here:
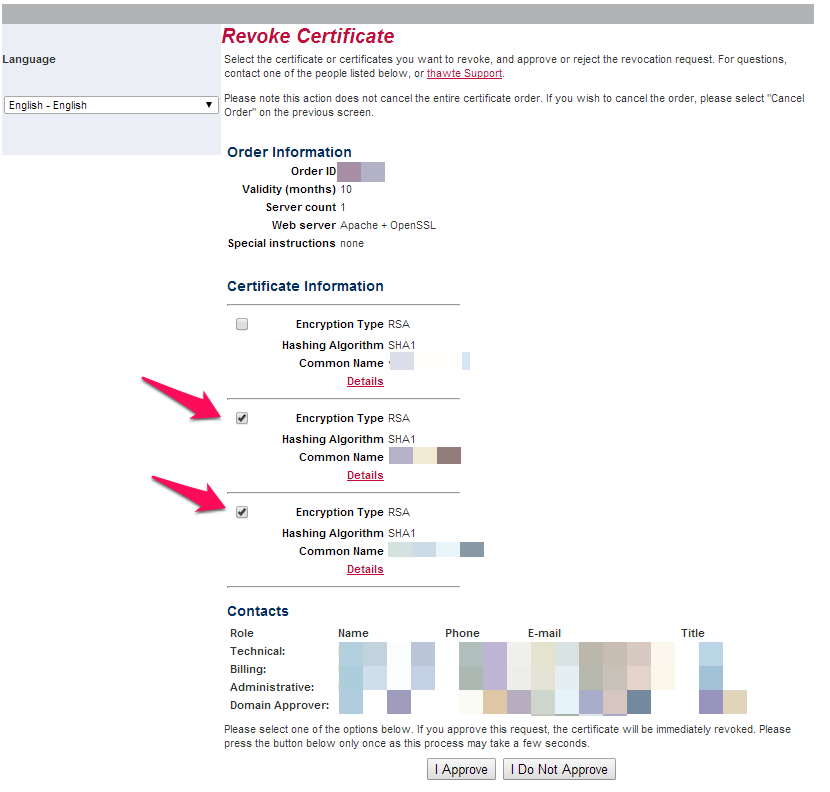
10. Click ?I Approve’ to complete the revocation request.
Revocation can take 24-48 hours after the request has been submitted for Comodo/ GeoTrust/RapidSSL Certificates and/or after the process has been initiated for Symantec/Thawte certificates. Once revocation is complete, your SSL Certificate will be fully secured.
